网友您好, 请在下方输入框内输入要搜索的题目:
题目内容
(请给出正确答案)
Questions 59-60 are based on the following information
A hash table With hash function
H1(k)=k mod 13
Is shown below.
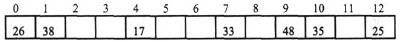
Collision is resolved using the hash function H2(k)=(k mod 11)+1
How many key comparisons occur in searching for key 35 in the given hash table?
A.0
B.1
C.2
D.3
参考答案
更多 “ Questions 59-60 are based on the following informationA hash table With hash functionH1(k)=k mod 13Is shown below.Collision is resolved using the hash function H2(k)=(k mod 11)+1How many key comparisons occur in searching for key 35 in the given hash table?A.0B.1C.2D.3 ” 相关考题
考题
考虑一个特殊的hash函数h,能将任一字符串hash成一个整数k,其概率P(k)=2^(-k),k=1,2,…,∞。对一个未知大小的字符串集合S中的每一个元素取hash值所组成的集合为h(S)。若h(S)中最大的元素Maxh(S)=10,那么S的大小的期望是()A.1024B.512C.5D.10
考题
Which three are properties of the MyISAM storage engine?()
A.Transaction supportB.FULLTEXT indexing for text matchingC.Table and page level locking supportD.Foreign key supportE.Geospatial indexingF.HASH index supportG.Table level locking only
考题
设线性表(59,53,46,48,37,31,25)采用散列(Hash)法进行存储和查找,散列函数为H(Key)=Key MOD 7(MOD表示整除取余运算)。若用链地址法解决冲突(即将相互冲突的元素存储在同一个单链表中)构造散列表,则散列表中与哈希地址 (38) 对应的单链表最长。A.2B.3C.4D.6
考题
All three types of cryptography schemes have unique function mapping to specific applications. For example, the symmetric key( ) approach is typically used for the encryption of data providing ( ) , whereas asymmetric key cryptography is mainly used in key ( ) and nonrepudiation , thereby providing confidentiality and authentication. The hash ( ) (noncryptic), on the other hand, does not provide confidentiality but provides message integrity, and cryptographic hash algorithms provide message ( ) and identity of peers during transport over insecure channels.A.CryptographyB.decodeC.privacyD.security@@@SXB@@@A.ConductionB.confidenceC.confidentialityD.connection@@@SXB@@@A.AuthenticationB.structureC.encryptionD.exchange@@@SXB@@@A.AlgorithmB.SecureC.structureD.encryption@@@SXB@@@A.ConfidentialityB.integrityC.serviceD.robustness
考题
散列地址空间为0..(m-1),k为关键字,用整数p去除k,将其余数作为k的散列地址,即hash(k)=k%p。为了减少发生冲突的可能性,一般取p为(35)。A.小于等于m的最大奇数B.小于等于m的最大质数C.小于等于m的最大偶数D.小于等于m的最大合数
考题
Cisco Express Forwarding (CEF) is mainly used to increase packet switching speed, reducing the overhead and delays introduced by other routing techniques, increasing overall performance.Which of the following concerning CEF is recommended by Cisco?()A. Use default Layer 4 hash in core.B. Use default Layer 3 hash in distribution.C. Use default Layer 4 hash in distribution.D. Use default Layer 3 hash in core and Layer 3 + Layer 4 hash in distribution layer.
考题
● 若线性表(24, 13, 31, 6, 15, 18, 8)采用散列(Hash)法进行存储和查找,设散列函数为H(Key)=Key mod 11,则构造散列表时发生冲突的元素为 (1) 。(其中的mod表示整除取余运算)(1)A. 24和13B. 6 和15C. 6 和24D. 18和8
考题
All three types of cryptography schemes have unique function mapping to specific.For example, the symmetric key approach (71) is typically used for the encryption of data providing(72), whereas asymmetric key cryptography is maidy used in key(73)and nonrepudiation, thereby providing confidentiality and authentication. The hash(74)(noncryptic), on the other hand, does not provide confidentiality but provides message integrity, and cryptographic hash algorithms provide message(75)and identity of peers during transport over insecure channels.A. Cryptography
B.decode
C.privacy
D.security
考题
All three types of cryptography schemes have unique function mapping to specific.For example,the symmetric key approach( )is typically used for the encryption of data providing( ),whereas asymmetric key cryptography is maidy used in key( )and nonrepudiation,thereby providing confidentiality and authentication.The hash(本题)(noncryptic),on the other hand,does not provide confidentiality but provides message integrity,and cryptographic hash algorithms provide message( )and identity of peers during transport over insecure channels.A.Algorithm
B.Secure
C.structure
D.encryption
考题
Which two steps does a receiver perform to validate a message using HMAC? () A、 decrypts the received MAC using a secret keyB、 compares the computed MAC vs. the MAC receivedC、 authenticate the receivedmessage using the sender’s public keyD、 look up the sender’s public keyE、 extracts the MAC from the receivedmessage thenencrypts the received message with a secret keyto producethe MACF、 Computes the MAC using the receivedmessage and a secret key as inputs to the hash function
考题
The enable secret password appears as an MD5 hash in a router’s configuration file, whereas the enablepassword is not hashed (or encrypted, if the password-encryption service is not enabled). What is thereason that Cisco still support the use of both enable secret and enable passwords in a router’sconfiguration?()A、The enable password is present for backward compatibility.B、Because the enable secret password is a hash, it cannot be decrypted. Therefore, the enable password is used to match the password that was entered, and the enable secret is used to verify that the enablepassword has not been modified since the hash was generated.C、The enable password is considered to be a router’s public key, whereas the enable secret password is considered to be a router’s private key.D、The enable password is used for IKE Phase I, whereas the enable secret password is used for IKE Phase II.
考题
Which data organization schemes are supported?()A、PARTITION BY HASH and ORGANIZE BY B、PARTITION BY RANGE and ORGANIZE BY KEY SEQUENCE C、PARTITION BY HASH and ORGANIZE BY KEY SEQUENCE D、PARTITION BY RANGE and ORGANIZE BY
考题
设有一个含有13个元素的Hash表(0~12),Hash函数是:H(key)=key%13,其中%是求余数运算。用线性探查法解决冲突,则对于序列(2、8、31、20、19、18、53、27),18应放在第几号格中()。A、5B、9C、4D、0
考题
通过hash 掩码方式实现RP 的负载分担,以下描述正确的有() A、 不同路由器上hash 掩码可以不同。B、 hash 掩码由各路由器自己设置。C、 hash 掩码由BSR 生成。D、 hash 掩码方式下,RP 的选择与C-RP 优先级无关。
考题
Server load balancing (SLB) is the process of deciding to which server a load-balancing device should send a client request for service. Which predictors are supported on ACE in order to select the best server to fulfill a client request? ()A、 Hash address: Selects the server by using a hash value based on either the source or destination IP address, or bothB、 Hash URL: Selects the server by using a hash value based on the requested URLC、 Hash MAC.Selects the server by using a hash value based on either the source or destination MAC address, or bothD、 Hash header: Selects the server by using a hash value based on the HTTP header nameE、 Hash IP: Selects the server using a hash value based on the IP address
考题
Which of the following commands should be used to assure that a dump can be forced using the reset button on a system without a key switch?()A、sysdumpdev -k B、sysdumpdev -L C、sysdumpdev -K D、sysdumpdev -P
考题
In which scenario will you create a sorted hash cluster? ()A、 if the application uses queries joining tables only occasionallyB、 if the full table scan is executed often on only one table of the clustered tablesC、 if the data for all the rows of a cluster key value exceeds one or two Oracle blocksD、 when you want the data to be returned automatically in the chronological order
考题
Which three are properties of the MyISAM storage engine?()A、Transaction supportB、FULLTEXT indexing for text matchingC、Table and page level locking supportD、Foreign key supportE、Geospatial indexingF、HASH index supportG、Table level locking only
考题
单选题Which of the following commands should be used to assure that a dump can be forced using the reset button on a system without a key switch? ()A
sysdumpdev -k B
sysdumpdev -L C
sysdumpdev -K D
sysdumpdev -P
考题
多选题Server load balancing (SLB) is the process of deciding to which server a load-balancing device should send a client request for service. Which predictors are supported on ACE in order to select the best server to fulfill a client request? ()AHash address: Selects the server by using a hash value based on either the source or destination IP address, or bothBHash URL: Selects the server by using a hash value based on the requested URLCHash MAC.Selects the server by using a hash value based on either the source or destination MAC address, or bothDHash header: Selects the server by using a hash value based on the HTTP header nameEHash IP: Selects the server using a hash value based on the IP address
考题
单选题Cisco Express Forwarding (CEF) is mainly used to increase packet switching speed, reducing theoverhead and delays introduced by other routing techniques, increasing overall performance.Which of the following concerning CEF is recommended by Cisco?()A
Use default Layer 4 hash in core.B
Use default Layer 3 hash in distribution.C
Use default Layer 4 hash in distribution.D
Use default Layer 3 hash in core and Layer 3 + Layer 4 hash in distribution layer.
考题
多选题Which two steps does a receiver perform to validate a message using HMAC? ()Adecrypts the received MAC using a secret keyBcompares the computed MAC vs. the MAC receivedCauthenticate the receivedmessage using the sender’s public keyDlook up the sender’s public keyEextracts the MAC from the receivedmessage thenencrypts the received message with a secret keyto producethe MACFComputes the MAC using the receivedmessage and a secret key as inputs to the hash function
热门标签
最新试卷