考题
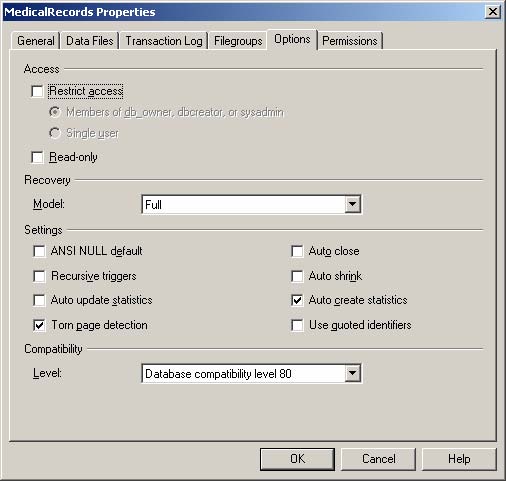
You are the database administrator of a SQL Server 2000 computer. The server contains your company's Accounts database. Hundreds of users access the database each day.Because you have had power interruptions in the past, you want to perfect the physical integrity of the Accounts database. You do not want to slow down server operations.What should you do?A.Enable the torn page detection database option for each database.B.Disable write caching on all disk controllers.C.Ensure that write caching disk controllers have battery backups.D.Create a database maintenance plan to check database integrity and make repairs each night.
考题
You are the administrator of a SQL Server 2000 computer. The server contains database named Sales. Users report that they cannot add new data to the database. You examine the properties of the database. The database is configured as shown in the Sales Properties exhibit.You examine drive E. The hard disk is configured as shown in the Local Disk Properties exhibit.You want the users to be able to add data, and you want to minimize administrative overhead. What should you do?A.Increase the maximum file size of Sales_Data to 1,500MB.B.Use the DBCC SHRINKDATABASE statement.C.Set automatic file growth to 10 percent.D.Create another data file named Sales_Data2 in a new SECONDARY filegroup.
考题
You are the administrator of several SQL Server 2000 computers. You want to retrieve information from an archived inventory database. You have a full tape backup of the database. The backup’s header information shows that the backup uses the SQL_Latin1_General_CR437_BIN collation.However, the existing SQL server computers in your office are configured to use theSQL_Latin1_General_CP1_CI_AS collation.You do not want to join tables in the inventory database with tables in other databases. You need to restore the inventory database to a SQL Server 2000 computer by using the least amount of administrative effort.What should you do?A.Use the rebuildm utility to rebuild the system database on an existing SQL server computer. Configure all the databases on that server to use the SQL_Latin1_General_CR437_BIN collation. Restore the inventory database to the server.B.Restore the inventory database to an existing SQL server computer. Accept the SQL_Latin1_General_CR437_BIN collation for that database.C.Install a new named instance of SQL Server 2000 on an existing SQL Server 2000 computer. Configure the named instance to use the SQL_Latin1_General_CR437_BIN collation. Restore the inventory database to the named instance.D.Install SQL Server 2000 on a new computer. Configure the new server to use the SQL_Latin1_General_CR437_BIN collation. Restore the inventory database to the new server.
考题
You are the network administrator for All network servers run either Windows 2000 Server or Windows Server 2003, and all client computers run Windows XP Professional.A computer named Server2 runs Windows Server 2003 with IIS 6.0 installed. On Server2, you create a virtual directory named WebFolder. You use IIS Manager to enable the following permissions on WebFolder: Read, Write, and Directory Browsing.When users try to access WebFolder as a Web folder from Internet Explorer, they receive the error message shown in the exhibit.You need to ensure that all users can access WebFolder as a Web folder.What should you do?()A. Restart the World Wide Web Publishing Service on Server2.B. Enable anonymous access to WebFolder.C. Modify the Execute permissions to allow scripts and executable files.D. Enable the WebDAV Web service extension on Server2.
考题
You work in a company which uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. There is a database named named Dworks in the instance. The Dworks table has a table named BillDetails which has a clustered primary key named BillId on the BillId column. The BillDetails table has a single XML column named GoodsDetails. The XML column has an XML index and XML data are stored in this XML column. A new column named GoodsID is added to the BillDetails table. GoodsID must be included in the primary key. So what action should you perform to achieve this goal?() A、You should drop the XML index on the table. Modify the primary key. Recreate the XML index B、You should alter the XML index and set the ALLOW_ROW_LOCKS = OFF option. Alter the primary key and set the ALLOW_ROW_LOCKS = ON option. C、You should move the XML data to a temporary table. Clear the XML data from the original table by setting the GoodsDetails column to NULL. Modify the primary key. Repopulate the ProductSpecs column. D、You should disable the XML index on the GoodsDetails column. Modify the primary key.Enable the XML index on the ProductSpecs column.
考题
Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2. The domain contains a member server named Server1. Server1 has the File Server server role installed. On Server1, you create a share named Documents. The Documents share will contain the files and folders of all users. You need to ensure that when the users connect to Documents, they only see the files to which they have access. What should you do?()A、Modify the NTFS permissionsB、Modify the Share permissionsC、Enable access-based enumerationD、Configure Dynamic Access Control
考题
A new employee needs access to a SQL Server 2005 database that is located on a server named SQL1. You create a login named ajones by using the following Transact-SQL statement. CREATE LOGIN ajones WITH PASSWORD = ’SQLServer$1’ The new employee reports that when he logs in, he receives the following error message: "Login failed. The user is not associated with a trusted SQL Server connection." You need to resolve the error and allow the new employee to gain access to SQL1. What should you do?()A、Change the SQL Server security mode from Windows Authentication mode to SQL Server and Windows authentication mode.B、Change the SQL Server security mode from SQL Server and Windows Authentication mode to Windows authentication mode.C、Ensure that the login name is created with square brackets ([]).D、Give the login access to a specific database by using the CREATE USER Transact-SQL statement.
考题
our network contains a Web server named Server1 that runs Windows Server 2003 and Internet Information Server (IIS). Server1 has a server certificate from an Enterprise Certificate Authority (CA) installed.External users report that when they try to access the Web site from outside the corporate network by using a Web browser, they receive the following warning message: “There is a problem with this Web site’s security certificate. The security certificate presented by this Web site was not issued by a trusted certificate authority.” You find that users on the corporate network do not receive this error.You need to ensure that external users do not receive the warning message when connecting to Server1. What should you do?()A、In IIS Manager, enable the Enable client certificate mapping option. B、In IIS Manager, replace the certificate with a certificate obtained from a public Certification Authority. C、In Local Security Policy, enable Domain Member: Require strong (Windows 2000 or later) session key. D、In Local Security Policy, enable Domain Member: Digitally encrypt or sign secure channel data
考题
You are the administrator of a SQL Server 2005 computer named SQL1. All servers run Microsoft Windows Server 2003 and belong to a Microsoft Active Directory domain. The companys written security policy mandates strong passwords for all domain, local, and application accounts. The appropriate domain password policy has been deployed through the use of a Group Policy object (GPO). Many of the company’s computers run MS-DOS-based or UNIX-based operating systems. These computers require varying levels of access to a database named Services on SQL1. You need to ensure that these computers can access the Services database without violating the company’s written security policy. What should you do?()A、Create a domain account for each of the company’s users. Provide each domain account with access to SQL1 and the Services database.B、Create a local logon account on SQL1 for each of the company’s users. Provide each logon account with access to SQL1 and the Services database.C、Create a SQL Server logon account for each of the company’s users. Enable the Enforce password policy option for each logon account. Provide each logon account with access to the Services database.D、Configure a virtual directory through Internet Information Services (IIS) for access to SQL1. Direct users to the virtual directory for data access.E、Create one SQL Server logon account for all of the company’s computers running MS-DOS or UNIX-based operating systems. Enable the Enforce password policy option for users’ accounts. Provide the logon accounts with access to the Services database.
考题
You are the network administrator for your company. The network consists of a single Active Directory domain. The network contains Windows Server 2003 file servers. The network also contains a Windows Server 2003 computer named Server1 that runs Routing and Remote Access and Internet Authentication Service (IAS). Server1 provides VPN access to the network for users’ home computers. You suspect that an external unauthorized user is attempting to access the network through Server1. You want to log the details of access attempts by VPN users when they attempt to access the network. You want to compare the IP addresses of users’ home computers with the IP addresses used in the access attempts to verify that the users are authorized. You need to configure Server1 to log the details of access attempts by VPN users. What should you do? ()A、 Configure the system event log to Do not overwrite.B、 In IAS, in Remote Access Logging, enable the Authentication requests setting.C、 Configure the Remote Access server to Log all events.D、 Create a custom remote access policy and configure it for Authentication-Type.
考题
You work in a company which is named Wiikigo Corp. The company uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. There is a computer which hosts several applications in your company. The instance runs on the computer. A job named DiliveryList is created by you. This job requires a file to be written to a file server. But because the job cannot access the file server, it fails to run. You intend to configure the SQL Server Agent service so that only the SQL Server Agent service has read and write access to the file server. Which account type should you use? () A、You should use local Service accountB、You should use network Service accountC、You should use domain accountD、You should use local System account
考题
Your corporate network has a member server named RAS1 that runs Windows Server 2008 R2. You configure RAS1 to use the Routing and Remote Access Services (RRAS).The companys remote access policy allows members of the Domain Users group to dial in to RAS1. The company issues smart cards to all employees.You need to ensure that smart card users are able to connect to RAS1 by using a dial-up connection.What should you do?()A、Install the Network Policy Server (NPS) server role on RAS1.B、Create a remote access policy that requires users to authenticate by using SPAP.C、Create a remote access policy that requires users to authenticate by using EAP-TLS.D、Create a remote access policy that requires users to authenticate by using MS-CHAP v2.
考题
Your corporate network has a member server named RAS1 that runs Windows Server 2008. You configure RAS1 to use the Routing and Remote Access Service (RRAS) The companys remote access policy allows members of the Domain Users group to dial in to RAS1. The company issues smart cards to all employees. You need to ensure that smart card users are able to connect to RAS1 by using a dial-up connection. What should you do?()A、 Install the Network Policy Server (NPS) on the RAS1 serverB、 Create a remote access policy that requires users to authenticate by using SPAPC、 Create a remote access policy that requires users to authenticate by using EAP-TLSD、 Create a remote access policy that requires users to authenticate by using MS-CHAP v2
考题
You have an Exchange Server 2010 organization. The organization contains two servers named Server1 and Server2. Server1 and Server2 have the Mailbox server role and the Hub Transport server role installed. Server 1 and Server2 are members of a database availability group (DAG). You need to plan the deployment of Client Access servers to meet the following requirements: .Users must be able to access their mailboxes if a single server fails .Users must not attempt to connect to a failed server What should you include in your plan?()A、On Server1 and Server2, install the Client Access server role. Implement failover clustering.B、On Server1 and Server2, install the Client Access server role. Configure network interface card (NIC) teaming on each server.C、Deploy two new Client Access servers. Implement load balancing by using DNS round robin.Create a Client Access server array.D、Deploy two new Client Access servers. Implement load balancing by using a Windows Network Load Balancing cluster. Create a Client Access server array.
考题
You are the network administrator for your company. The network consists of a single Active Directory domain. The network contains an application server running Windows Server 2003. Users report intermittent slow performance when they access the application server throughout the day. You find out that the network interface on the application server is being heavily used during the periods of slow performance. You suspect that a single computer is causing the problem.You need to create a plan to identify the problem computer. What should you do?()A、 Monitor the performance monitor counters on the application server by using System Monitor. B、 Monitor the network traffic on the application server by using Network Monitor.C、 Monitor network statistics on the application server by using Task Manager.D、 Run network diagnostics on the application server by using Network Diagnostics.
考题
You are the administrator of an Active Directory domain. All servers run Windows Server 2003. All client computers run Windows XP Professional and are members of the domain.The domain contains a single DNS server named Server1. Root hints are enabled on Server1. Internet access for the company is provided by a Network Address Translation (NAT) server named Server2. Server2 is connected to the Internet by means of a permanent connection to the company’s ISP.Users report that they can no longer connect to http://www.adatum.com. Users can connect to internal resources and to other Internet Web sites. You can successfully access http://www.adatum.com from a computer outside of the corporate network.You need to ensure that the users can access http://www.adatum.com. You must also ensure that users retain their ability to access internal resources. Which two actions should you perform?()A、Disable Routing and Remote Access on Server2.B、Create a root zone on Server1.C、On all affected users’ computers, run the ipconfig /flushdns command.D、Configure all affected users’ computers to use the ISP’s DNS server.E、Use the DNS console on Server1 to clear the DNS cache.
考题
our network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1 that runs Windows Server 2012 R2. Server1 contains a shared folder named Share1. Share1 contains the home folder of each user. All users have the necessary permissions to access only their home folder. The users report that when they access Share1, they can see the home folders of all the users. You need to ensure that the users see only their home folder when they access Share1. What should you do from Server1?()A、From Windows Explorer,modify the properties of the volume that contains Share1.B、From Server Manager,modify the properties of the volume that contains Share1.C、From Server Manager,modify the properties of Share1.D、From Windows Explorer,modify the properties of Share1.
考题
ou work in a company which is named Wiikigo Corp. The company uses SQL Server 2008. You are the administrator of the company database. Now for a new application, a SQL Server 2008 instance has to be installed on an existing server. The server contains a default SQL Server 2005 instance. Your company CIO wants their corresponding certified third-party applications can access to both database instances. The company assigns this task to you. You must achieve this by using as little database administrative effort as possible, and never change the existing application environments. What should you do? () A、You should install SQL Server 2008 as the default instance, and configure the new application to use the default instance B、You should upgrade the SQL Server 2005 application to use SQL Server 2008 C、You should upgrade the SQL Server 2005 instance to a SQL Server 2008 instance D、You should install SQL Server 2008 as a named instance, and make the new application use the new instance.
考题
Your network contains two Active Directory sites named Site1 and Site2. Only Site1 can be accessed from the Internet. You have an Exchange Server 2010 organization. You deploy a Client Access server in Site1 and enable Windows Integrated Authentication for OutlookWeb App (OWA). In Site2, you deploy a Mailbox server and a Client Access server. You need to configure the Exchange organization to meet the following requirements: .Allow users to access their mailboxes from the Internet by using OWA .Prevent authentication prompts from displaying when users connect to OWA by using domain- joinedcomputers that are connected to the internal network What should you do?()A、Modify the Exchange virtual directory on the Client Access server in Site1.B、Modify the Exchange virtual directory on the Client Access server in Site2.C、Modify the OWA virtual directory on the Client Access server in Site1.D、Modify the OWA virtual directory on the Client Access server in Site2.
考题
You have an Exchange Server 2010 organization.Your network contains two Active Directory sites named Site1 and Site2.Each site contains five Mailbox servers.A Mailbox server named Server1 is in Site1.A Mailbox server named Server2 is in Site2.You have a public folder named Folder1 that is replicated to Server1 and Server2.Users in Site1 report that they cannot access Folder1 when Server1 is offline.You need to ensure that all users can access Folder1 if Server1 is offline.What should you do?()A、Add Server1 to the public folder referrals for Site2.B、Add Server2 to the public folder referrals for Site1.C、Add Server1 and Server2 to a Client Access server array.D、Add Server1 and Server2 to a database availability group (DAG).
考题
Your network contains two Active Directory sites named Site1 and Site2. Site1 contains a server named Server1. Server1 runs a custom application named App1.Users in Site2 report that they cannot access App1 on Server1. Users in Site1 can access App1.Server1 has a Windows Firewall with Advanced Security rule named Rule1.You discover that Rule1 blocks the connection to App1.You verify that Server1 has no connection security rules.You need to ensure that the Site2 users can connect to Server1.What should you modify in Rule1?()A、the authorized computers listB、the authorized users listC、the edge traversal settingsD、the scope
考题
You are a professional level SQL Server 2005 database administrator in an international corporation named Wiikigo. You are experienced in implementing high-availability solutions, monitoring the database server, and design deployment. In the company, you major job is the deployment, maintenance and support of Microsoft SQL Server 2005. You work as the administrator of a SQL Server 2005 computer, and the computer is named SQL1. Microsoft Windows Server 2003 is run by all servers. All the servers belong to a Microsoft Active Directory domain. According to the company written security policy, strong passwords are mandated for all domain, local, and application accounts. The company utilizes a Group Policy object (GPO) to deploy the proper domain password policy. MS-DOS-based or UNIX-based operating systems are run by many of the company’s computers. Varying levels of access to a database named Services on SQL1 is requested by the computers. Since you are the database administrator, you are required to confirm that the Services database can be accessed by these computers. And the company’s written security policy should not be violated. Which action should be performed by you?()A、A domain account should be created for each of the company’s users. And then, each domain account should be offered with access to SQL1 and the Services database.B、A local logon account should be created on SQL1 for each of the company’s users. And then, each logon account should be offered with access to SQL1 and the Services database.C、One SQL Server logon account should be created for all of the company’s computers running MS-DOS or UNIX-based operating systems. And then, the Enforce password policy option should be enabled for users’ accounts. At last, the logon accounts should be provided with access to the Services database.D、A SQL Server logon account should be created for each of the company’s users. And then, the Enforce password policy option should be enabled for each logon account. At last, each logon account should be offered with access to the Services database.E、A virtual directory should be configured through Internet Information Services (IIS) for access to SQL1. And then, users should be directed to the virtual directory for data access.
考题
You create a Microsoft ASP.NET application by using the Microsoft .NET Framework version 3.5. The application contains a DataSourceControl named CategoriesDataSource that is bound to a Microsoft SQL Server 2005 table. The CategoryName column is the primary key of the table. You write the following code fragment in a FormView control: 01 02 Category: 03 09 10 You need to ensure that the changes made to the CategoryID field can be written to the database. Which code fragment should you insert at line 04?()A、SelectedValue='%# Eval("CategoryID") %' B、SelectedValue='%# Bind("CategoryID") %' C、SelectedValue='%# Eval("CategoryName") %' D、SelectedValue='%# Bind("CategoryName") %'
考题
You work in a company which uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance on the same physical computer. Now users report that they are unable to connect to the named instances. You check and verify that they can only connect to the default instance. You also ensure that all SQL Server instances run normally. You have to start the service which is required to connect to the named instances. Which service should you start?() A、Server B、SQL Server Agent C、SQL Server Browser D、SQL Active Directory Helper
考题
Your network contains two Active Directory sites named Site1 and Site2. Only Site1 can be accessed from the Internet. You have an Exchange Server 2010 organization. You deploy a Client Access server in Site1 and enable Windows Integrated Authentication for OutlookWeb App (OWA). In Site2, you deploy a Mailbox server and a Client Access server. You need to configure the Exchange organization to meet the following requirements: .Allow users to access their mailboxes from the Internet by using OWA .Prevent authentication prompts from displaying when users connect to OWA by using domain- joined computers that are connected to the internal network What should you do?()A、Modify the Exchange virtual directory on the Client Access server in Site1.B、Modify the Exchange virtual directory on the Client Access server in Site2.C、Modify the OWA virtual directory on the Client Access server in Site1.D、Modify the OWA virtual directory on the Client Access server in Site2.
考题
单选题Your corporate network has a member server named RAS1 that runs Windows Server 2008. You configure RAS1 to use the Routing and Remote Access Service (RRAS) The companys remote access policy allows members of the Domain Users group to dial in to RAS1. The company issues smart cards to all employees. You need to ensure that smart card users are able to connect to RAS1 by using a dial-up connection. What should you do?()A
Install the Network Policy Server (NPS) on the RAS1 serverB
Create a remote access policy that requires users to authenticate by using SPAPC
Create a remote access policy that requires users to authenticate by using EAP-TLSD
Create a remote access policy that requires users to authenticate by using MS-CHAP v2
考题
单选题You work in a company which uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. There is a database named named Dworks in the instance. The Dworks table has a table named BillDetails which has a clustered primary key named BillId on the BillId column. The BillDetails table has a single XML column named GoodsDetails. The XML column has an XML index and XML data are stored in this XML column. A new column named GoodsID is added to the BillDetails table. GoodsID must be included in the primary key. So what action should you perform to achieve this goal?()A
You should drop the XML index on the table. Modify the primary key. Recreate the XML index B
You should alter the XML index and set the ALLOW_ROW_LOCKS = OFF option. Alter the primary key and set the ALLOW_ROW_LOCKS = ON option. C
You should move the XML data to a temporary table. Clear the XML data from the original table by setting the GoodsDetails column to NULL. Modify the primary key. Repopulate the ProductSpecs column. D
You should disable the XML index on the GoodsDetails column. Modify the primary key.Enable the XML index on the ProductSpecs column.