备考干货丨2020年想要报考ACCA的你需要了解这些
发布时间:2019-12-29
号外!号外!号外!
听说有很多小伙伴想要报考ACCA,但又不知道具体的规定和条件是什么?
没有关系,51题库考试学习网帮你收集到了你想知道的所有消息,且随51题库考试学习网一起去了解一下,看看你能否加入ACCA大家庭:
(一)报名条件
报名注册ACCA 考试,具备以下条件之一即可:
1、凡具有教育部承认的大专以上学历,即可报名成为ACCA 的正式学员;
2、教育部认可的高等院校在校生,顺利完成大一的课程考试,即可报名成为ACCA 的正式学员;
3、未符合1、2项报名资格的16周岁以上的申请者,也可以先申请参加FIA 基础财务资格考试。在完成基础商业会计(FAB)、基础管理会计(FMA)、基础财务会计(FFA)3门课程,并完成ACCA 基础职业模块,可获得ACCA 商业会计师资格证书,资格证书后可豁免ACCAF1-F3 三门课程的考试,直接进入技能课程的考试。
(二)考试流程
一、填写注册表
1、请登陆ACCA官方网站填写英文注册信息,进行网上注册。网上注册指南请见:ACCA网上注册指引( 文件下载)
2、获得英文注册编号后,登录ACCA官方中文网站请用中文填写中文学员登记表。
二、提供注册所需资料
①学历/学位证明(高校在校生需提交学校出具的在校证明函及第一年所有课程考试合格的成绩单)的原件、复印件和译文;外地申请者不要邮寄原件,请把您的申请材料复印件加盖公司或学校公章,或邮寄公证件既可。
②身份证的原件、复印件和译文;或提供护照,不需提交翻译件。
③一张两寸照片;(黑白彩色均可)
④注册报名费(银行汇票或信用卡支付),请确认信用卡可以从国外付款,否则会影响您的注册返回时间;如果不能确定建议您用汇票交纳注册费。(信用卡支付请在英文网站上注册时直接输入信用卡详细信息,英国总部收到您的书面注册材料后才会从您的信用卡上划账)。
三、交纳报名注册费
报名注册费以双币信用卡或者银行汇票的方式交纳。具体办理汇票方法如下:
凭身份证到有外汇业务和英镑汇票业务的银行办理换汇和汇票业务。其中"汇款回单"中左上方请选择"票汇D/D",在"收款人"一栏中只要填入ACCA即可。 不需填写英国方面的账号信息。
四、到代表处办理报名注册程序
将填写完整的网上报名注册表(在英文网站上注册完成后可以打印出两页的PDF文件)、中文学员登记表请先打印再点击提交,以及其他相关材料交至代表处或直接寄往英国总部。
五、报名注册反馈
一般通过代表处注册两个月后ACCA UK会将以下材料寄到代表处,由代表处转发给学员:
1.、免试通知(如果有免试)
2.、登记卡:有学员照片和学员注册号的学员身份证明,参加考试时出示给监考官。
3.、确认函:学员注册号、密码及考卷类型的确认通过ACCA代表处注册成为ACCA学员以后,ACCA英国总部将按照学员在ACCA报名注册表中所填写的通讯地址直接通过邮寄材料和通知的形式与学员直接联系。学员还会在2月底、3月初和8月底、9月初收到考试报名表,办理考试报名;在考试前2周左右收到准考证。
信用卡及国际汇票: ACCA的注册费、年费、考试费用可以使用双币信用卡及国际汇票办理。
推荐使用的双币信用卡有中国银行及招商银行双币信用卡。
国际汇票可至任何一家有外汇业务的银行(推荐至中国银行办理),凭本人身份证办理。
(三)注册所需材料
一、在校学生
1、中英文在校证明
(原件)
2、中英文成绩单 (可复印加盖所在学校或学校教务部门公章)
3、中英文个人身份证件或护照 (复印件加盖所在学校或学校教务部门公章)
4、2寸彩色护照用证件照一张
5、用于支付注册费用的国际双币信用卡或国际汇票 (推荐使用Visa)
二、非在校学生(符合学历要求)
1、中英文个人身份证件或护照
(复印件加盖第三方章)
2、中英文学历证明(复印件加盖第三方章)
3、2寸彩色护照用证件照一张
4、用于支付注册费用的国际双币信用卡或国际汇票 (推荐使用Visa)
三、非在校学生(不符合学历要求- FIA形式)
1、中英文个人身份证件或护照
(复印件加盖第三方章)
2、2寸彩色护照用证件照一张
3、用于支付注册费用的国际双币信用卡或国际汇票 (推荐使用Visa)
(四)ACCA注册时间
注册报名随时都可以进行,但注册时间的早晚,决定了第一次参加考试的时间。注册完成后必须在官方考试报名截止前获得审核,才可以参加考试报名。
(五)考试规则
ACCA考试规则
1、申请参加ACCA考试者,必须首先注册成为ACCA学员。
2、学员必须按考试大纲设置的先后次序报考,即知识课程,技能课程,核心课程和选修课程。在一个课程阶段中可以选择任意顺序报考。但ACCA建议在一个课程中也按照顺序报考。
3、除免试和已通过的课程外,每次或者每个考试期(6个月内)最多报考4门。
4、核心课程的3个科目无须同时报考
5、基础阶段的知识课程考试时间为两小时,基础阶段的技能课程和专业阶段所有课程考试时间为三小时,及格成绩为50分(百分制),每科成绩合格后予以保留。
6、所有14门考试必须在学员第一次考试通过后10年内完成。(单科成绩有效期为10年)
7、以FIA途径注册的学员,可以在注册完成后,选择完成FAB,FAM,FFA,可以申请转入ACCA并且豁免F1-F3三门课程的考试,直接进入ACCA技能课程阶段的考试。
以上就是报考ACCA的具体规则和流程,想要了解更多2020年ACCA的相关资讯,欢迎加入关注51题库考试学习网。
下面小编为大家准备了 ACCA考试 的相关考题,供大家学习参考。
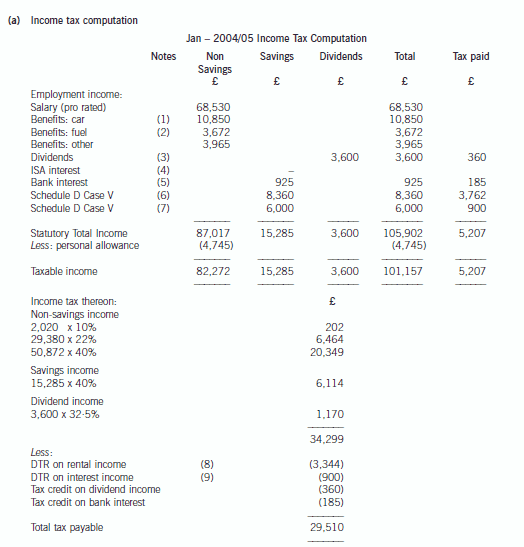
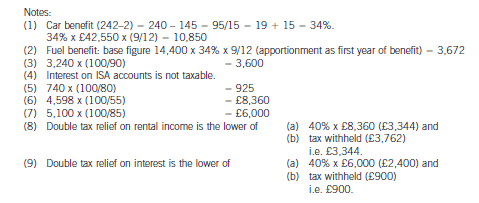
2 Assume that today’s date is 1 July 2005.
Jan is aged 45 and single. He is of Danish domicile but has been working in the United Kingdom since 1 May 2004
and intends to remain in the UK for the medium to long term. Although Jan worked briefly in the UK in 1986, he
has forgotten how UK taxation works and needs some assistance before preparing his UK income tax return.
Jan’s salary from 1 May 2004 was £74,760 per annum. Jan also has a company car – a Jaguar XJ8 with a list price
of £42,550 including extras, and CO2 emissions of 242g/km. The car was available to him from 1 July 2004. Free
petrol is provided by the company. Jan has other taxable benefits amounting to £3,965.
Jan’s other 2004/05 income comprises:
£
Dividend income from UK companies (cash received) 3,240
Interest received on an ISA account 230
Interest received on a UK bank account 740
Interest remitted from an offshore account (net of 15% withholding tax) 5,100
Income remitted from a villa in Portugal (net of 45% withholding tax) 4,598
The total interest arising on the offshore account was £9,000 (gross). In addition, Jan has not remitted other
Portuguese rental income arising in the year, totalling a further £1,500 (gross).
Jan informs you that his employer is thinking of providing him with rented accommodation while he looks for a house
to buy. The accommodation would be a two bedroom flat, valued at £155,000 with an annual value of £6,000. It
would be made available from 6 August 2005. The company will pay the rent of £600 per month for the first six
months. All other bills will be paid by Jan.
Jan also informs you that he has 25,000 ordinary shares in Gilet Ltd (‘Gilet’), an unquoted UK trading company. He
has held these shares since August 1986 when he bought 2,500 shares at £4.07 per share. In January 1994, a
bonus issue gave each shareholder nine shares for each ordinary share held. In the last week all Gilet’s shareholders
have received an offer from Jumper plc (‘Jumper’) who wishes to acquire the shares. Jumper has offered the following:
– 3 shares in Jumper (currently trading at £3.55 per share) for every 5 shares in Gilet, and
– 25p cash per share
Required:
(a) Calculate Jan’s 2004/05 income tax (IT) payable. (11 marks)
(ii) Assuming the new structure is implemented with effect from 1 August 2006, calculate the level of
management charge that should be made by Bold plc to Linden Limited for the year ended 31 July
2007, so as to minimise the group’s overall corporation tax (CT) liability for that year. (2 marks)
(ii) For the year ended 31 July 2007, there will be two associated companies in the group. Bold plc will count as an
associated company as it is not dormant throughout the period in question. As a result, the corporation tax limits will be
divided by two (i.e. the number of associates) giving an upper limit of £750,000 (£1·5 million/2). As Linden Limited
is anticipated to make profits of £1·4 million in the year to 31 July 2007 it will pay corporation tax at the rate of 30%.
Bold plc can earn trading profits up to £150,000 (£300,000/2) and pay tax at the rate of 19%. It will therefore
minimise the group’s corporation tax liability if maximum use is made of this small companies rate band, as it will save
£16,500 (150,000 x (30% – 19%)) of corporation tax for the year to 31 July 2007. Bold plc should therefore make
a management charge of sufficient size to give it profits for that year equal to £150,000.
While the transfer pricing legislation no longer applies to small and medium sized enterprises, Bold plc should
nevertheless ensure that there is evidence to support the actual charge made in terms of the services provided.
(c) Using sensitivity analysis, estimate by what percentage the life cycle of the Snowballer would need to change
before the recommendation in (a) above is varied. (4 marks)

This information was taken from an internal newsletter of The Knowledge Partnership LLP (TKP), a company which offers project and software consultancy work for clients based in Zeeland. The newsletter was dated 2 November 2014 and describes two projects currently being undertaken by the partnership.
Project One
In this project, one of our clients was just about to place a contract for a time recording system to help them monitor and estimate construction contracts when we were called in by the Finance Director. He was concerned about the company supplying the software package. ‘They only have an annual revenue of $5m’, he said, ‘and that worries me.’ TKP analysed software companies operating in Zeeland. It found that 200 software companies were registered in Zeeland with annual revenues of between $3m and $10m. Of these, 20 went out of business last year. This compared to a 1% failure rate for software companies with revenues of more than $100m per year. We presented this information to the client and suggested that this could cause a short-term support problem. The client immediately re-opened the procurement process. Eventually they bought a solution from a much larger well-known software supplier. It is a popular software solution, used in many larger companies.
The client has now asked us to help with the implementation of the package. A budget for the project has been agreed and has been documented in an agreed, signed-off, business case. The client has a policy of never re-visiting its business cases once they have been accepted; they see this as essential for effective cost control. We are currently working with the primary users of the software – account managers (using time and cost data to monitor contracts) and the project support office (using time and cost data to improve contract estimating) – to ensure that they can use the software effectively when it is implemented. We have also given ‘drop in’ briefing sessions for the client’s employees who are entering the time and cost data analysed by the software. They already record this information on a legacy system and so all they will see is a bright new user interface, but we need to keep them informed about our implementation. We are also looking at data migration from the current legacy system. We think some of the current data might be of poor quality, so we have established a strategy for data cleansing (through offshore data input) if this problem materialises. We currently estimate that the project will go live in May 2015.
Project Two
In this project, the client is the developer of the iProjector, a tiny phone-size projector which is portable, easy to use and offers high definition projection. The client was concerned that their product is completely dependent on a specialist image-enhancing chip designed and produced by a small start-up technology company. They asked TKP to investigate this company. We confirmed their fears. The company has been trading for less than three years and it has a very inexperienced management team. We suggested that the client should establish an escrow agreement for design details of the chip and suggested a suitable third party to hold this agreement. We also suggested that significant stocks of the chip should be maintained. The client also asked TKP to look at establishing patents for the iProjector throughout the world. Again, using our customer contacts, we put them in touch with a company which specialises in this. We are currently engaged with the client in examining the risk that a major telephone producer will launch a competitive product with functionality and features similar to the iProjector.
The iProjector is due to be launched on 1 May 2015 and we have been engaged to give advice on the launch of the product. The launch has been heavily publicised, a prestigious venue booked and over 400 attendees are expected. TKP have arranged for many newspaper journalists to attend. The product is not quite finished, so although orders will be taken at the launch, the product is not expected to ship until June 2015.
Further information:
TKP only undertakes projects in the business culture which it understands and where it feels comfortable. Consequently, it does not undertake assignments outside Zeeland.
TKP has $10,000,000 of consultant’s liability insurance underwritten by Zeeland Insurance Group (ZIG).
Required:
(a) Analyse how TKP itself and the two projects described in the scenario demonstrate the principles of effective risk management. (15 marks)
(b) Describe the principle of the triple constraint (scope, time and cost) on projects and discuss its implications in the two projects described in the scenario. (10 marks)
(a) The first stages of risk management are the identification, descriptions and assessment of the risk. This assessment is primarily concerned with the likelihood of them occurring and the severity of impact on the organisation or project should they occur. Sometimes the likelihood is a subjective probability, the opinions of experienced managers or experts in the field. On other occasions, there is some statistical evidence on which to base the assessment. For example, in project 1, TKP identified that 20 IT software companies with annual revenues between $3m and $10m went out of business last year. This represented 10% of the total number of software companies reporting such revenues. Its report to the client suggested that there was a 10% chance of the current preferred supplier (who had a turnover of $5m) ceasing business and this would have a significant short-term support implication. This compared to a business failure rate of 1% for software companies with an annual revenue exceeding $100m. The client felt that the probability of supplier failure was too high, so eventually bought a software solution from a much larger, well-known, software supplier. In this case, the likelihood of the risk led the client to changing its procurement decision. The risk itself does not go away, large companies also fail, but the probability of the risk occurring is reduced.
The avoidance (or prevention) of a risk is a legitimate risk response. In project 1, the client could avoid the risk ‘failure of the supplier’ by commissioning an in-house bespoke solution. Similarly, TKP itself avoids the risks associated with trading in different cultures, by restricting its projects to clients based in Zeeland.
There are three further responses to risks.
Risk mitigation (or risk contingency) actions are what the organisation will do to counter the risk, should the risk take place. Mitigation actions are designed to lessen the impact on the organisation of the risk occurring. In project 2, TKP recommends that the producers of the iProjector should establish an escrow agreement with the company which produces the chip which enhances the quality of the projected image. It was agreed that design details of this chip should be lodged with a third party who would make them available to the producers of the iProjector should the company which owned the enhanced image technology cease trading. This is a mitigation approach to the risk ‘failure of the supplier’. The supplier is relatively high risk (less than three years of trading, inexperienced management team), and the product (the iProjector) is completely dependent upon the supply of the image enhancing chip. The failure of the business supplying the chips would have significant impact on iProjector production. If the escrow agreement had to be enacted, then it would take the producers of the iProjector some time to establish alternative production. Consequently (and TKP have suggested this), it might be prudent to hold significant stocks of the chips to ensure continued production. In such circumstances, the need to mitigate risk is more important than implementing contemporary just-in-time supply practices. In some instances a mitigation action can be put in place immediately. In other instances risk mitigation actions are only enacted should the risk occur. The risk has been recognised and the organisation has a rehearsed or planned response. For example, in project 1, TKP has identified ‘poor quality of current data’ as a risk associated with the migration of data from the current systems to the proposed software package solution. It has established a strategy for data cleansing if that risk actually materialises. Importantly, the client knows in advance how to respond to a risk. It avoids making a hasty, ill-thought out response to an unforeseen event.
Risk transfer actions are concerned with transferring the risk and the assessment and consequences of that risk to another party. This can be done in a number of ways. TKP itself has liability insurance which potentially protects the company from the financial consequences of being sued by clients for giving poor advice. TKP has identified this as a risk, but is unlikely to be able to assess either the probability of that risk occurring or establishing meaningful mitigation measures to minimise the effect of that risk. Consequently, the responsibility for both of these is transferred to an insurance company. They establish the risk, through a series of questions, and compute a premium which reflects the risk and the compensation maximum which will have to be paid if that risk occurs. TKP pays the insurance premiums. TKP itself also transfers risks in project 2. It is unsure about how to establish patents and so it refers the client to another company. Transferring avoids the risk associated with ‘establishing the patent incorrectly’ and the financial consequences of this.
Finally, risk may be identified but just accepted as part of doing business. Risk acceptance is particularly appropriate when the probability of the risk is low or the impact of that risk is relatively insignificant. Risks may also be accepted when there are no realistic mitigation or transfer actions. In project 2, the producers of the iProjector are concerned that there is ‘a risk that a major telephone producer will launch a product with features and functionality similar to ours’. This is a risk, but there is little that can be done about it. Risks of competition are often best accepted.
The discussion above is primarily concerned with deciding what action to take for each risk. Once these actions are agreed, then a plan may be required to put them into place. For example, establishing an escrow agreement will require certain activities to be done.
Risks must also be monitored. For example, in project 2, the risk of supplier failure can be monitored through a company checking agency. Many of these companies offer a continuous monitoring service which evaluates financial results, share prices and other significant business movements. Reports are produced, highlighting factors which may be of particular concern. Risks will also disappear once certain stages of the project have been completed and, similarly, new ones will appear, often due to changes in the business environment. Many organisations use a risk register or risk log to document and monitor risks and such logs often specify a risk owner, a person responsible for adequate management of the risk.
(b) Every project is constrained in some way by its scope, time and cost. These limitations are often called the triple constraint. The scope concerns what has to be delivered by the project, time is when the project should deliver by, and cost is concerned with how much can be spent on achieving the deliverable (the budget). Quality is also an important feature of projects. Some authors include quality in their triple constraint (instead of scope), others add it as a further constraint (quadruple constraint), whilst others believe that quality considerations are inherent in setting the scope, time and cost goals of a project. How a particular project is managed depends greatly on the pressures in the triple constraint.
In project 1, the reluctance of the company to re-visit the business case means that the budget (or cost) of the solution is fixed. The implementation date might be desirable, but it does not seem to be business critical. It is an internal system and so any delays in implementation will not affect customers. It will also be a relatively seamless transition for most employees in the company. They already record the time record details which the new system will collect and so all they will see is a changed user interface. Only the direct users of the output (account managers and the project office) will be affected by any delay. The scope of the software package is also pre-defined. If it fails to meet requirements, then the users will have to adjust their expectations or business methods. There is no money to finance customisation or add-on systems, so in this sense the scope of the solution is also fixed. The quality of the software, in terms of its reliability and robustness, should also be good, as it is a popular software solution used in many large companies.
In project 2, the launch date is fixed. It has been heavily publicised, the venue is booked and over 400 attendees are expected, including newspaper journalists. Thus the time of the project is fixed. However, although orders will be taken at the launch, the product is not expected to ship until a month after launch. Thus the scope of the product shown at the launch date might be restricted and inherent quality problems might not yet be solved. Any defects can be explained away (this is a pre-production model) or, more effectively, they may be avoided by ensuring that the product is demonstrated to attendees, not used by them. The project manager must ensure that key functionality of the product is available on launch date (such as producing an image of a certain quality), but other functionality, not central to the presentation (for example, promised support for all image file formats) could be delayed until after the presentation. The company should make extra funds available to ensure that the launch date is successful.
声明:本文内容由互联网用户自发贡献自行上传,本网站不拥有所有权,未作人工编辑处理,也不承担相关法律责任。如果您发现有涉嫌版权的内容,欢迎发送邮件至:contact@51tk.com 进行举报,并提供相关证据,工作人员会在5个工作日内联系你,一经查实,本站将立刻删除涉嫌侵权内容。
- 2020-01-03
- 2020-01-09
- 2020-12-31
- 2021-01-13
- 2020-01-09
- 2021-04-07
- 2020-01-30
- 2020-08-15
- 2020-01-09
- 2021-04-02
- 2021-01-13
- 2020-03-25
- 2020-08-15
- 2021-04-02
- 2020-02-27
- 2020-01-10
- 2020-07-04
- 2021-02-13
- 2020-01-09
- 2020-01-09
- 2021-04-25
- 2020-02-28
- 2020-09-03
- 2020-02-18
- 2021-01-13
- 2021-04-04
- 2020-09-03
- 2020-08-14
- 2020-01-10
- 2020-01-09